SAML 2.0
This section is complementary to Step 11 in Installing the Web Application and Distribution.
It is possible to associate Nectari to an SSO server using the SAML2 protocol.
SAML2 does not work with Web Central Point Configurator and DataSync.
SAML2 is only available for On-Premise installation.
Many service providers offer SSO.
For example, the following procedure is given by Microsoft for Azure SSO (click here for more details).
- Add an unlisted application Azure AD Single Sign-On.
- Enter the following information:
- Sign on URL: Nectari login URL (e.g. https://yourserver:81) .
- Identifier: This URI must match the SEI Issuer URI configuration made when installing the package (e.g. https://yourserver:81/webclient) .
- Reply URL: Nectari connection page (e.g. https://yourserver:81).
- The next screen provides the following information:
- A certificate to save in: C:\inetpub\wwwroot\WebClient\App_Data.
- Issuer URL: Copy and paste to the line ID Provider Issuer Name.
- Single Sign-ON Service URL: Copy and paste to the line ID Provider URL.
- Single Sign-OUT: Note that Single Sign Out is currently not available. Sign out of Nectari has to be done in its own application.
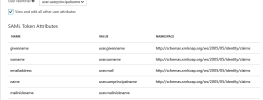
NoteA field with the login for Nectari must also be defined. This name has to match with the line for SAML2 answer’s attribute for user name. This is used for SSO with Active Directory.
ExampleHere is an example where the name is mailnickname. More details on this setting can be found here.
- Authorize users to use the application. They will then be able to connect to Nectari at the same time as their other services.
Web browsers have updated their policy regarding cookies and these changes must be applied to your Web Client if you want Nectari embedded into your ERP website, or use Single Sign-On (SSO). Refer to Cookie Management for more details.